I just noticed a couple of tweets where file recovery software developers such as iCare and Easeus went as far as: “Save $300 in your pocket and don’t pay the ransom to decrypt files!”. For a moment I was under the impression, that they already figured out how to decrypt the hostage files. But that’s not the case. So, is it possible to recover files from the Wannacrypt ransomware?
Don’t let them fool you, it is just cheap exposure and marketing tactics. They do not offer special versions of their software, nothing like that. The claim is that you can recover your files using undelete software. They post blog articles with titles like “How to recover WannaCrypt encrypted files” to attract visitors and potential customers. Some even offer free versions of their software, but these are just limited versions that will only recover upto a certain amount. Typically 1 or 2 GB, which is nothing given the fact that the virus will encrypt much more than that. To recover more than the one or 2 free GB you will of course need to purchase a license.
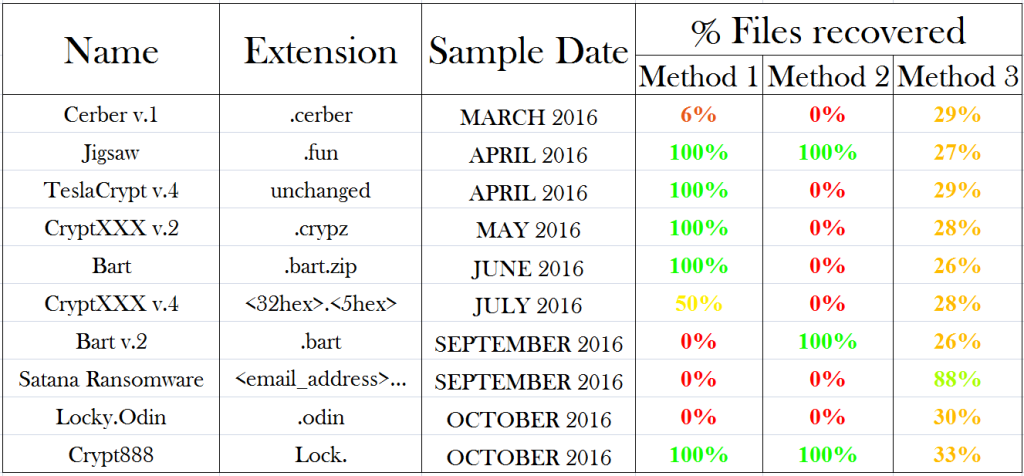
Note that for specific Ransomware viruses decrypters are available. If a decrypter is available you can probably recover 100% of your data. Here’s another list of ransomware for which decryption tools are available.
Also some variants do not delete Windows Shadow Copies, and you may be able to recover all your data (not with Wannacrypt). A nice free tool explore Windows Shadow Copies can be found here.
Now, the million Dollar question, can you recover data from a ransomware crypto or data-locker virus attack using conventional file recovery software?
The short answer:
Small scale testing suggests that on average you may be able to recover 30% of the original files deleted by the ransomware intact using file recovery software.
Update specific to Wannacrypt
Update 1
While next paragraphs are valid in general when dealing with ransomware, more info specific on how to recover files from the Wannacrypt virus is becoming available:
“Files stored in Desktop, My Documents, or on any removable disks in the computer at the time of the infection are overwritten with randomly generated data and deleted. This means it is not possible to recover them with a file undelete or disk recovery tool. However, due to possible weaknesses in the malware it is possible to recover other encrypted files on the system when they were stored outside of these three locations, using an undelete of disk recovery tool, as most of the files are moved to a temporary folder and then normally deleted, without being overwritten by a wiper. ” – source
Source verified their findings using DiskDrill, according to the developer you’ll be needing their Pro version ($89). I believe that there is no reason to not try Recuva or DiskTuna DFR instead (see bottom page) which can be used for free.
Update 2
Under circumstances it is possible to decrypt files. Needs luck, Windows XP or Windows 7. And you should NOT have rebooted your PC as it depends on certain information used to encrypt to still be present in memory.
https://blog.comae.io/wannacry-decrypting-files-with-wanakiwi-demo-86bafb81112d.
https://github.com/gentilkiwi/wanakiwi
Crypto ransomware viruses – how they work (many of them).
I will not address how your PC is infected and how the viruses or worms spread, nor removal and disinfection of your machine. This is a quick and dirty article and I got the information from various sources, and I focus on how to recover files from (the wannacrypt) ransomware. It is how I understand many of the ransomware viruses work. I will describe the file operations that take place once the virus executes and starts encrypting your data. To do so it needs to use standard Windows file operations. Typically this is how it works:
Open the ‘victim’ file
Read file data into memory
Create a new file and write encrypted data
Delete the original file
So, their promise to be able to recover you data lies in the fact that those deleted files can be recovered. They do not decrypt the encrypted files.
Undelete or deleted file recovery
If a deleted file can be recover depends on two factors:
- Is the file entry still intact?
- Are the clusters allocated to the file untouched
When a file is deleted, the file entry is ‘flagged’ as ‘not in use’. Also, the clusters previously being allocated to the file are marked as free for use in the $Bitmap. Under normal circumstances, with typical file system IO on an in use system there is already a fair chance that the file entry is used for another file, or data from another file is written to clusters previously allocated to the deleted file. The golden rules therefor are always to try to prevent writes to the file system, and to recover the deleted file as quickly as possible.
Now, imagine the amount of file system IO as a result of the virus itself and it becomes clear that recovery of the original, non-encrypted files is far from certain! There is a more than high risk that file entries for the deleted files are used, and that data is written to clusters that were associated with the deleted files.
If you want to attempt the undelete method I suggest you use my DiskTuna DFR deleted file recovery software. It is fully functional shareware! You can try to recover all your data first, and then decide if it’s worth your money.
If it can not recover your data, then there is a microscopic chance that ReclaiMe File Recovery can using it’s RAW file recovery carving routines. Rather than relying on file entries it scans for characteristics of specific file types. See my article file system vs RAW file recovery.
Short answer to can I recover files from the wannacrypt ransomware
So, can recover files from the Wannacrypt ransomware? Small scale testing indeed suggests that on average you may be able to recover 30% of the files using file recovery software.
The preferred order to recover your data remains:
- Method 1: Check if a decryption utility is available. For example check here.
- Method 2: Check if Shadow Copies (Previous Versions) survived the attack. There are utilities available that make this easier.
- Method 3: Try Undelete or File Recovery Software.
DiskTuna DFR – Deleted File Recovery – Free Portable Undelete
https://www.disktuna.com/reclaime-data-recovery-software/