This is not a blogpost on the inner workings of this ransomeware. I am purely interested in discussing the recover-ability of your data. The Petya or NotPetya ransomware appears to do three things to prevent you access from your data:
- It encrypts the MBR
- Individual files files are encrypted
- Then it encrypts the Master File Table (MFT).
Encrypted MBR
This is normally not a big deal. Just make sure you don’t reboot from the hard disk after the MBR was encrypted as it will load the next portion of the ransomeware that will encrypt individual files and the MFT.
At this point recovery of data is very well possible using high quality file recovery software like ReclaiMe. Edit June 29: Assuming files themselves are not encrypted. Here’s where it gets confusing. Some claim files are already encrypted at this point. Some claim to have recovered files by preventing the reboot.
#Petya encrypts ON BOOT. If you see CHKDSK message your files not yet encrypted, power off immediately. You can recover with with LiveCD. pic.twitter.com/nKL4Xixjn9
— hackerfantastic.x (@hackerfantastic) June 27, 2017
Update June, 28, 1:26PM (CET): Seeing mixed messages here. Some claim that file encryption takes place BEFORE the reboot already. Example:
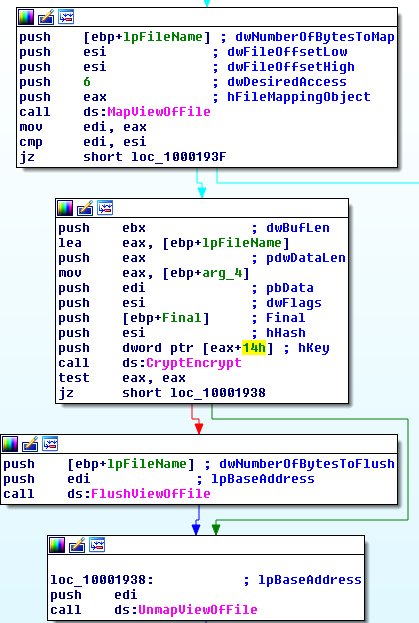
Encrypted files
Apart from decrypting the files it depends on the modus operandi of the Petya ransomeware if files are still recoverable to some degree. As we have seen with the WannaCry ransomeware, the original non-encrypted files *may* be recoverable using file recovery software. WannaCry opens the original files > writes encrypted data to a new file > and then deletes the original. The deleted files can be potentially undeleted.
So, the angle of attack would be to scan the file system form deleted files. On a NTFS drive this would imply scanning the MFT.
Update June, 28, 1:26PM (CET): It appears files are encrypted ‘in-place’. So no chance to recover the original files. Some one smarter than me sent me this as proof:
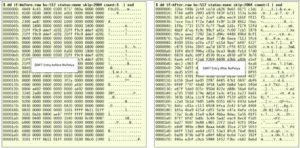
Encrypted MFT
The problem with that is, that Petya ransomware also encrypts the MFT after which it becomes impossible to scan it for deleted files.
Conclusion
If we assume the Petya ransomeware encrypts copies of the original files, after which originals are deleted, the only ‘angle of attack’ left is RAW file recovery. Again, this is an assumption at this point. And even with this assumption the chances to successfully recover data using file recovery software are very poor.
- If we assume files are encrypted after reboot, file recovery is possible as long as we prevent a reboot taking place.
- However, assuming files are encrypted before reboot, and the files are encrypted ‘in-place’, file recovery using file recovery software is impossible. With or without an encrypted MFT.
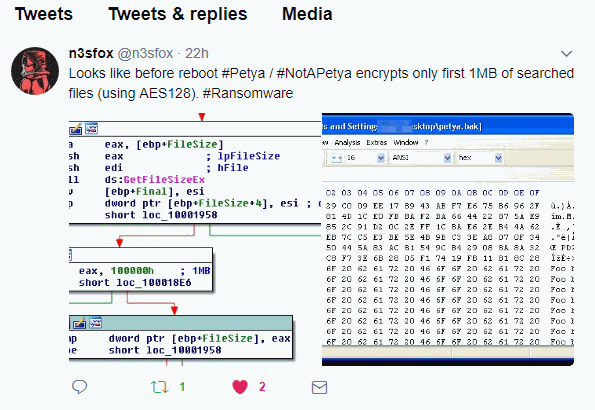
- If only the first MB of a file is encrypted file recovery using file recovery software may be impossible, however with a disk editor some data (not complete files) may be recovered.
Key is: What happened to the files themselves? Even without the MBR or MFT, files are theoretically recoverable as long as file contents remain intact.
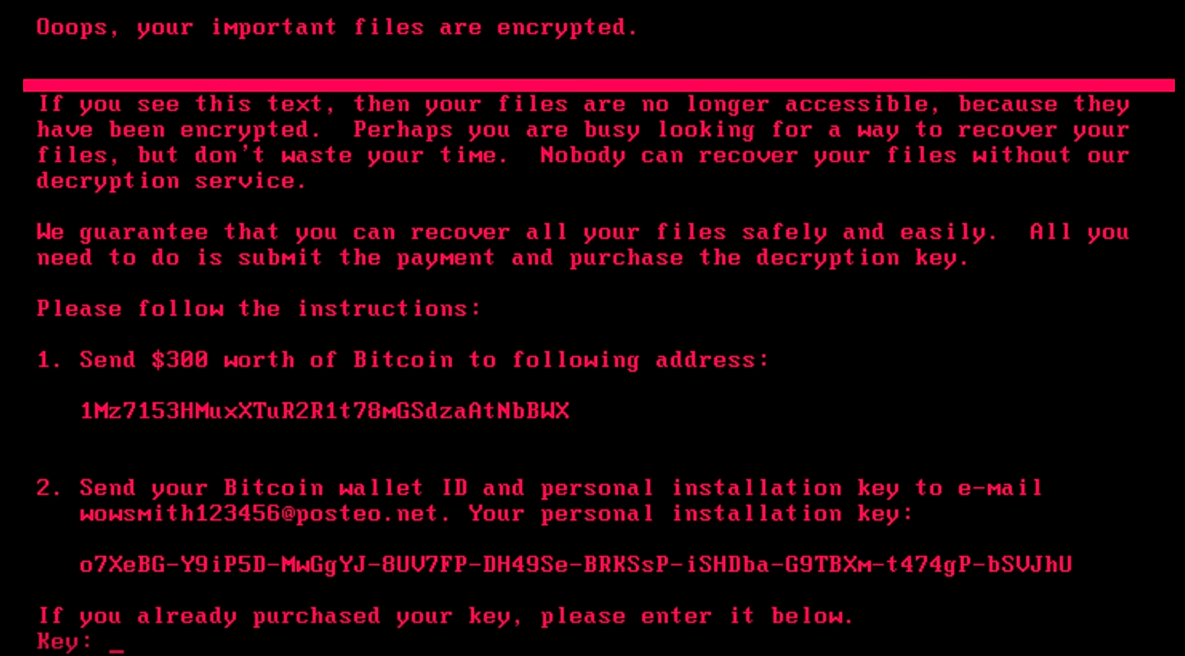
Please note that the fake boot time CHKDSK doesn’t look anything like the actual Windows boot time CHKDSK: