A case was brought to me as JPEGs encrypted by ransomware. This article shows repair of JPEGs that fell victim of ransomware. This particular ransomware only encrypts part of the file. Due to this the JPEG header and some 150 KB of JPEG data are lost. Using a reference file and after weeding encrypted data we can repair these photos. Repairing is done file by file, this is not an automatic process where 100’s of files are repaired with a single click.
Now, as this post is not to give anyone false hope, understand that fully encrypted files can not be ‘repaired’. The only repair possible is by decrypting such files. With some practice you’ll be able to repair one image per minute. JPEG-Repair was not designed or never intended as a specialized ransomware repair tool.
New! Media_Repair repairs audio and video files affected by STOP (DJVU) Ransomware (MP4, M4V, MOV, 3GP, WAV, MP3).
JPEGs encrypted by ransomware?
The customer that sent me the files told me the JPEGs can not be opened and no previews or thumbnails are visible. He suspects the JPEGs are encrypted by ransomware. Entropy however suggests files are at least not fully encrypted. About the 150 KB of each file contains non JPEG data. I didn’t investigate IF this was actual encrypted data, but indeed some ransomware encrypts only the start of files. The rest of the data looks like JPEG data entropy-wise and byte-histogram-wise.
Now, then it does not matter if the first 150 KB was encrypted or corrupted by whatever other data, if we have a valid header from a reference file we can use JPEG-Repair and see if we can make remaining JPEG data visible again. Only the encrypted portion of the data is lost. As this was only 150 KB of 6MB+ JPEG data a small strip of the photos can’t be repaired / recovered.
Only after I repaired 2 files I discovered that indeed the photos were partially encrypted by the STOP (Djvu) ransomware by using the ID-Ransomware website. I still document this case because the decryption tool does not work with all variants of the ransomware. It may also help with other ransomware that only partially encrypts files.
So: JPEGs encrypted by STOP/DJVU ransomware can be repaired provided you have a reference file. A reference file being an intact file shot with the same camera.
Repair using JPEG-Repair involves the following:
1. Append a valid header to corrupted file. This header must match JPEG data as closely as possible. So sample file needs to be shot with the same camera with settings matching as closely as possible. After appending the header and removing invalid JPEG Markers from the encrypted / corrupt data (done automatically by JPEG-Repair) the photo can be rendered.
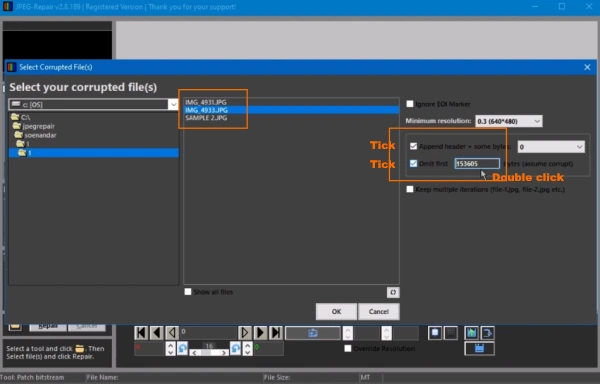
Select the corrupt (encrypted file) and tick option to append a header and to omit bytes. STOP ransomware encrypts 153605 bytes, double click text filed to automatically enter this value. Click OK. You’ll then be asked to select the reference file.
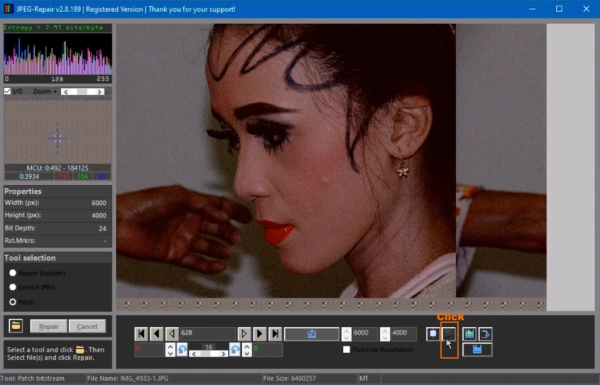
2. You’ll see the main screen with decoded JPEG. Image may be too dark/bright, color may be wrong and the image is not properly aligned. Click button to open MCU editor (see illustration).
3. Adjust alignment and color/brightness.
My order always is:
Click Auto-align, delete > click preview. If the image is still ‘off’ increae value for Delete and click preview until right.
the use sliders to adjust brightness and color. Again, move a slider and click preview. Once image looks good, click OK.
Video of the repair process:
Can JPEG-Repair help me?
Always first check if a decryptor is available. If so it’s by far the easiest way to repair your files.
Using the ID-Ransomware tool and uploading a JPEG I was able to determine we are dealing with the STOP (Djvu) ransomware for which a decryption tool is available. This tool does however not cover all variants of the ransomware. In those cases and other cases involving partial encryption you can use JPEG-Repair for repairing JPEGs encrypted by ransomware.
Partial or full encryption?
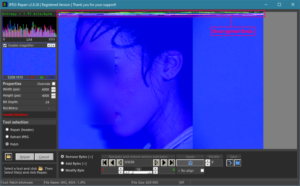
Let’s look at the image without first removing the encrypted data. We can see the encrypted data actually at the start of the image. So we can see wwith our own eyes how the file is only partially encrypted:
Tell tale signs that indicate partial encryption:
- Encrypted data at the start of the file looks very different and more distorted than actual image data. It stands out from the rest of the data.
- Entropy looks like entropy for a JPEG (top left above byte histogram). A full encrypted file would display an entropy value of 8.00 bits/byte
Also, JPEG-Repair can only help recover the part of the JPEG that is not encrypted. So for a full encrypted file there is nothing it can do.
Currently known file extensions for STOP Djvu
Note that this list may be outdated as new extensions keep appearing regularly!
| .STOP, .SUSPENDED, .WAITING, .PAUSA, .CONTACTUS, .DATASTOP, .STOPDATA, .KEYPASS, .WHY, .SAVEfiles, .DATAWAIT, .INFOWAIT,.djvut .pdff, .tro, .tfude, .tfudeq, .tfudet, .rumba, .adobe, .adobee, .blower, .promos, .promoz, .promock, .promoks, .promorad, .promorad2, .kroput, .kroput1, .charck, .pulsar1, .puma, .pumax, .pumas, .shadow, .djvu, .djvuu, .udjvu, .djvuq, .uudjvu, .djvus, .djvur, .klope, .kropun, .charcl, .doples, .luces, .luceq, .chech, .proden, .drume, .tronas, .trosak, .grovas, .grovat, .roland, .refols, .raldug, .etols, .guvara, .moresa, .verasto, .hrosas, .kiratos, .todarius, .hofos, .roldat, .dutan, .sarut, .fedasot, .browec, .norvas, .ferosas, .rectot, .skymap, .mogera, .rezuc, .stone, .redmat, .lanset, .davda, .poret, .pidon, .heroset, .myskle, .boston, .muslat, .gerosan, ,vesad, .horon, .neras, .dalle, .lotep, .nusar, .litar, .truke, .besub, .cezor, .lokas, .godes, .budak, .vusad, .herad, .berosuce, .gehad, .gusau, .madek, .tocue, .darus, .lapoi, .todar, .dodoc, .bopador, .novasof, .ntuseg, .nelasod, .mogranos, .cosakos, .nvetud, .lotej, .kovasoh, prandel, .zatrov, .masok, .ndarod, .access, .format, .brusaf, londec, .krusop, .nasoh, .nacro, .pedro, .mtogas, .coharos, .nuksus, .vesrato, .masodas, .stare, .cetori, .carote, .shariz, .gero, .hese, .geno, .seto, .peta, .moka, .meds, .kvag, .domn, .karl, .nesa, .boot, .kuub, .noos, .reco, .xoza, .bora, .leto, .werd, .nols, .coot, .derp, .nakw, .toec, .mosk, .lokf, .peet, .grod, .kodg, .mbed, .zobm, .rote, .msop, .hets, .righ, .gesd, .merl, .nbes, .mkos, .redl, .piny, .kodc, .nosu, .reha, .topi, .npsg, .btos, .repp, .alka, .bboo, rooe – Source: https://geeksadvice.com/remove-djvu-ransomware-virus/ |

The ransomware with extension (.prandel) has affected my files on my hard drive. what is the best way to recover my files back. How can i get my photos and videos… again?
The virus (.hets) has affected my files on my hard drive. what is the best way to recover my files back. How can i get my photos and videos… again?
It’s a STOP / DJVU family member. So same way as post and video demonstrate.
please help me..my laptop infected by DJVU variant ZATE..i can restore the mp3 using media repair from disk tuna..but the i have alot off Screen Recorder file mp4 using by filmora screen. I am Using For recorded Meeting Zoom, most 2 hours plus recording.. I can Repair it and Restore, using any kind of method or tool..using media repair only can restore several menit..please give advices what should i do??
Thank you
You can try using Stellar or WonderShare repair tools for video. In my tests they worked after providing a reference file.